Lab: Deploying a Vulnerable AWS EKS Infrastructure
In this lab, deploy a vulnerable AWS EKS infrastructure. The following steps will guide through setting up the infrastructure using bash script.
Step-by-Step Guide
- Navigate to the EKS Directory:
cd /workspaces/www-project-eks-goat/eks/
Ensure you have administrative privileges by configuring the AWS CLI using
aws configurewith your access and secret keys.
-
Input the following information:
- AWS Access Key ID
- AWS Secret Access Key
- Default region name (set to us-west-2 or us-east-1 based on your region)
- Default output format (choose json)
-
Validate AWS Administrative Privileges:
- Use the AWS STS (Security Token Service) to verify your identity and ensure you have the necessary permissions.
aws sts get-caller-identity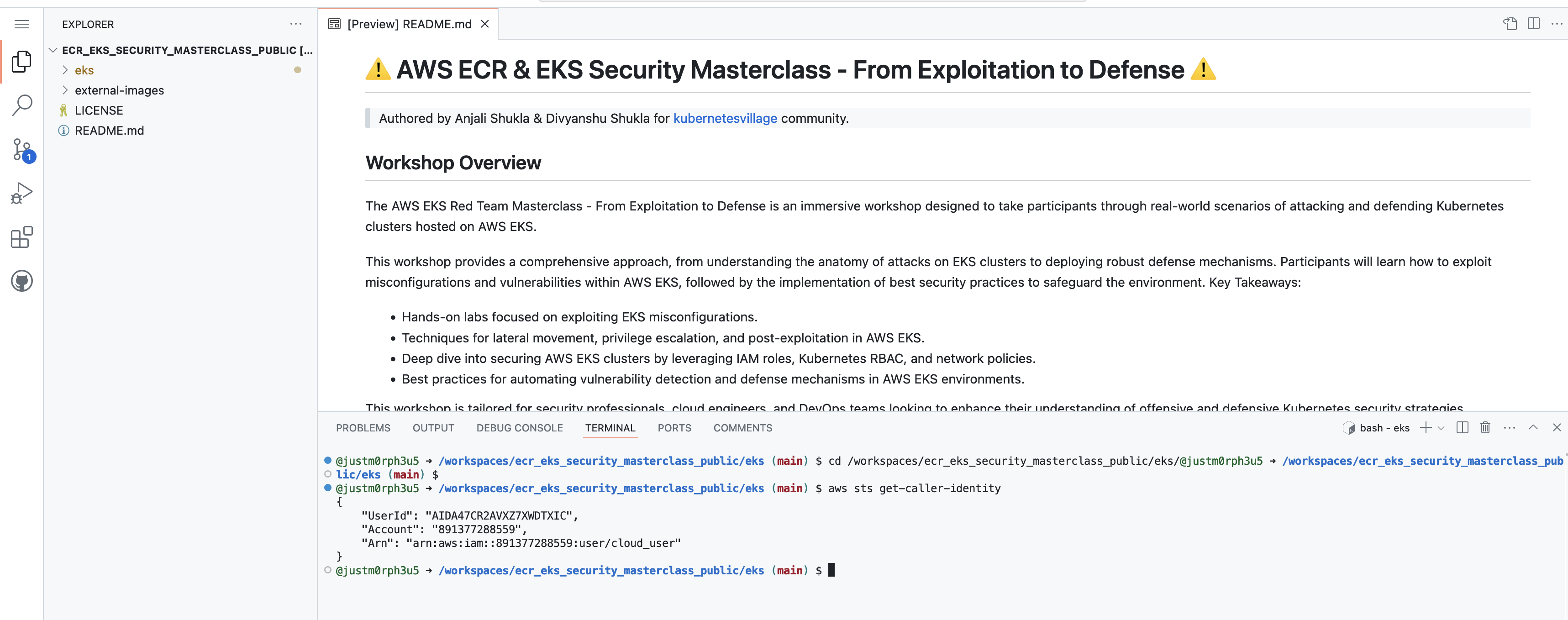
Ensure that AWS CLI is properly configured and have administrative privileges to deploy EKS clusters.
-
Run the Deployment Script:
- Deploy the vulnerable EKS infrastructure by running the deploy.sh script. You can specify a region using the --region flag. If no region is specified, it will default to us-west-2.
bash deploy.sh --region us-west-2
Select a different region, replace us-west-2 with the desired region like us-east-1. Currently us-east-1 & us-west-2 are supported.
-
Confirmation Prompt:
- Receive a confirmation prompt:
Do you want to continue with the deployment? (Y/N)- Type Y to proceed with the deployment.
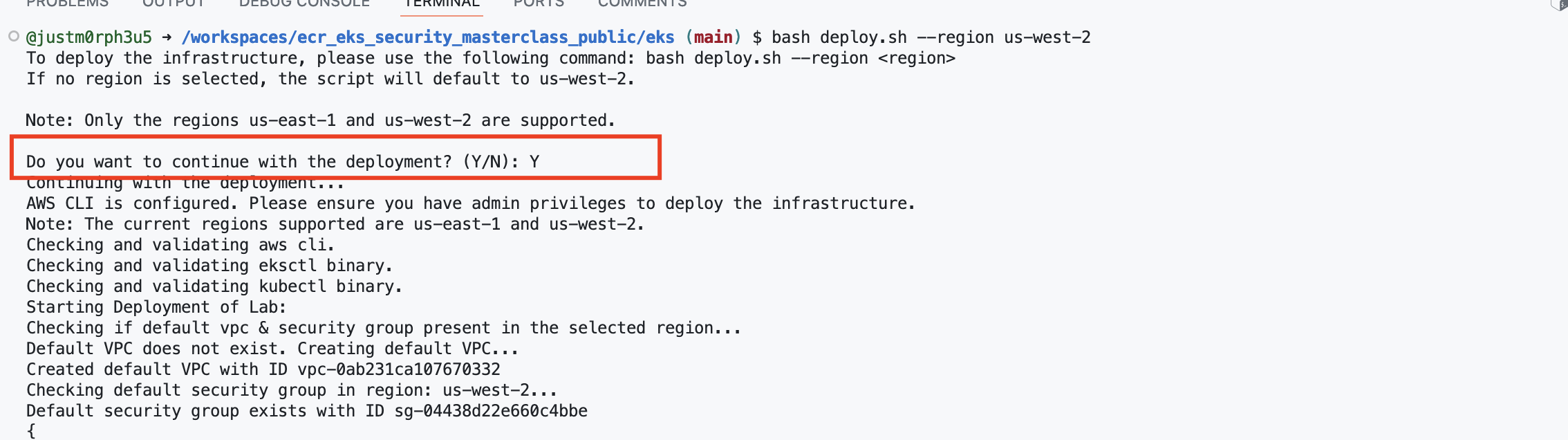
-
Deployment Process:
- The deployment process may take up to 15 minutes as it provisions the EKS cluster and associated resources.
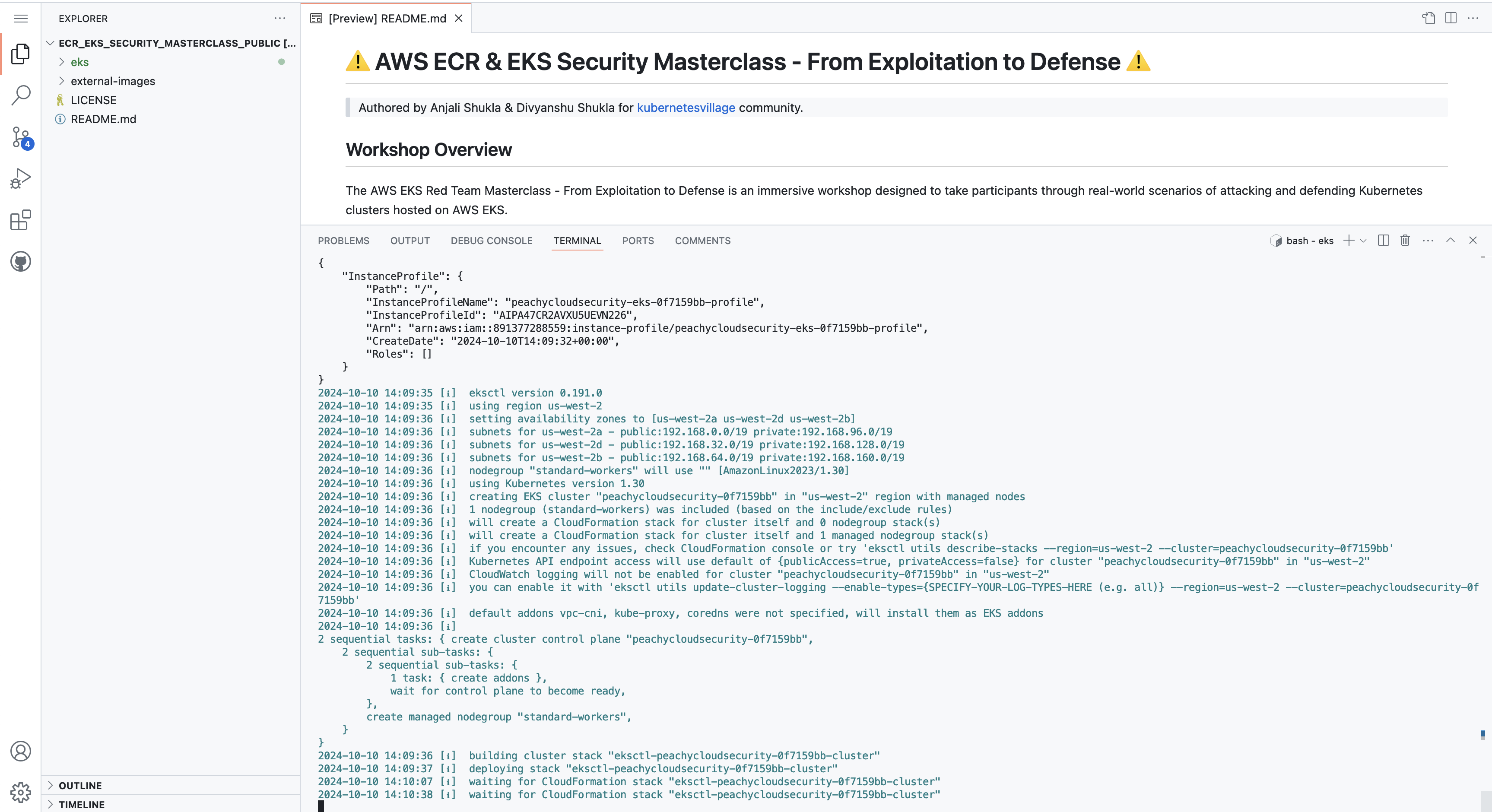
-
Final Output:
- After the deployment is complete, review the summary of the deployment, along with command for accessing the deployed EKS cluster.

-
Access the Vulnerable Application:
- After the deployment, you can access the vulnerable application via the public IP of the EC2 instance:
echo "Access the application at: http://$(jq -r '.instance_public_ip.value' < ec2_output.json)"
- After the deployment, you can access the vulnerable application via the public IP of the EC2 instance:
-
Configure the EKS Cluster.
echo "Authenticate to EKS cluster via: aws eks update-kubeconfig --region $(grep 'ECR Repository URL' deployment_output.txt | awk -F'.' '{print $4}') --name $(grep 'EKS Cluster Name' deployment_output.txt | awk '{print $4}')"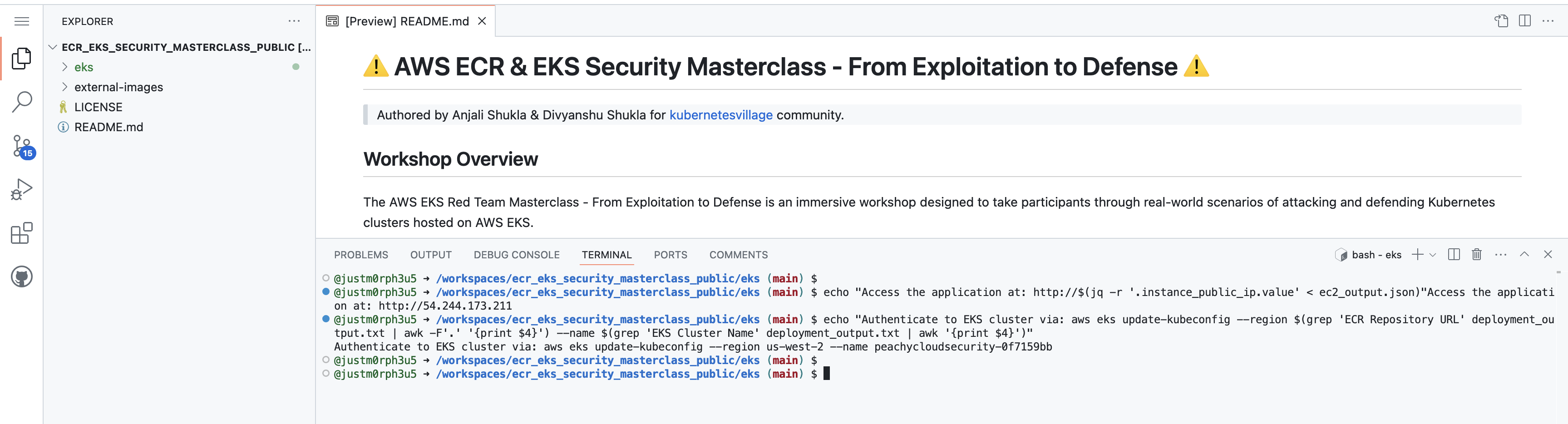
Optional
- To update the cni to v1.21.1, modify deploy.sh.
cat <<EOF > eks-cluster-config.yaml
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: ${EKS_CLUSTER_NAME}
region: ${REGION}
vpc:
clusterEndpoints:
publicAccess: true
privateAccess: false
upgradePolicy:
supportType: STANDARD
addons:
- name: vpc-cni
version: v1.21.1-eksbuild.1
configurationValues: |-
enableNetworkPolicy: "true"
managedNodeGroups:
- name: standard-workers
instanceType: t3.small
desiredCapacity: 2
minSize: 2
maxSize: 4
amiFamily: AmazonLinux2
iam:
instanceRoleARN: arn:aws:iam::${AWS_ACCOUNT_ID}:role/${EKS_ROLE_NAME}
EOF