Lab: Exploiting Sample Application
Exploiting real world application with CVE affecting AWS infra and thus exploiting EKS.
-
Change the current directory to the deployment directory
eks.cd /workspaces/www-project-eks-goat/eks/ -
Configure the EKS Cluster.
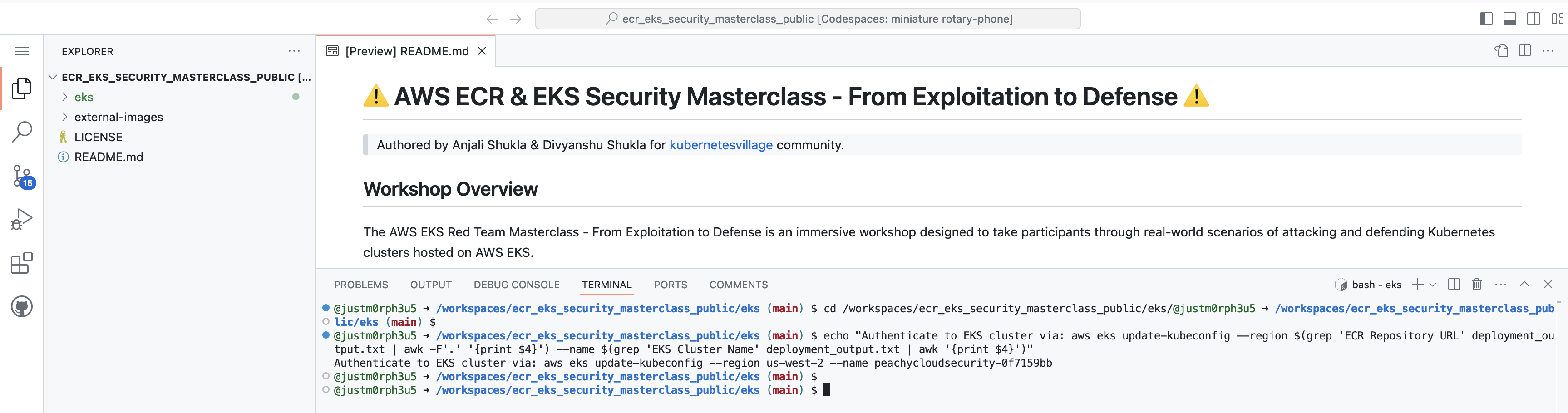
- Copy paste the command generated after this on the terminal to set AWS EKS Context
echo "Authenticate to EKS cluster via: aws eks update-kubeconfig --region $(grep 'ECR Repository URL' deployment_output.txt | awk -F'.' '{print $4}') --name $(grep 'EKS Cluster Name' deployment_output.txt | awk '{print $4}')"The command aws eks update-kubeconfig updates your local Kubernetes configuration (kubeconfig) file to include the AWS EKS cluster details.
The "Updated context," means that your local kubectl command will now be able to interact with the specified EKS cluster (peachycloudsecurity-{xxxxx}) using the correct credentials and settings for that cluster in the given region (us-west-2).
-
Access the Vulnerable Application:
-
After the deployment, you can access the vulnerable application via the public IP of the EC2 instance:
echo "Access the application at: http://$(jq -r '.instance_public_ip.value' < ec2_output.json)"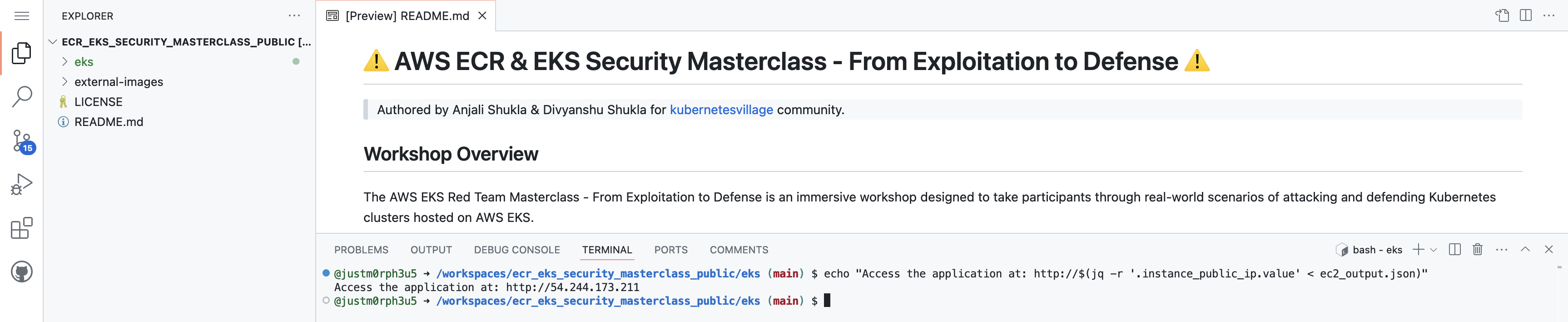
-
-
Copy paste the URL in the browser to start pentesting the web application to gain access to AWS Infra.
⚠️ DISCLAIMER: The next section of this lab contains the solution. If interested in challenges, STOP HERE and do not proceed to the next step. Try to exploit the application before checking the solution.
Credits for image: Offensive Security Say – Try Harder!
